Phishing attacks remain a prevalent technique employed by cybercriminals to compromise sensitive information. This article will help you to have a comprehensive understanding of different types of phishing attacks, their impact, and how to appropriately respond to them.

Introduction
Phishing stands out as the common form of cyber attack that specifically targets individuals using various communication channels, like emails text messages and phone calls. It falls under social engineering tactics, where perpetrators manipulate emotions and deceive people to acquire data. Perpetrators often pose as trusted sources to deceive people into sharing details such as bank account numbers or credit card information.
Phishing schemes may involve clicking on links, downloading and installing malicious files or sharing sensitive information. The ultimate aim of phishing scheme is to deceive the target into disclosing data, like details, login credentials or other sensitive information.
Content
Why Be Proactive and Vigilant?
Strategies Used in Phishing Attacks
Email Phishing
Spear Phishing
Smishing and Vishing
Impact of Phishing Attacks
Prevention and Mitigation of Phishing Attacks
Preventive Measures
Reporting of Suspicious Phishing Activities
FAQ
Conclusion
Phishing Quiz
Key Takeaways
- Phishing attacks are a common and persistent threat that requires constant attention and awareness.
- Phishing attacks can be categorized into email phishing, spear phishing, smishing, and vishing.
- Common tactics used in phishing attacks include social engineering techniques, such as creating a sense of urgency and using character substitution in domain names.
- Falling victim to phishing scams can lead to financial losses, mental distress, and productivity decline.
- Financial data, such as banking logins, PINs, account numbers, and credit card details, are often targeted by phishers.
- Ransomware and other malware are distributed through phishing attacks, causing system outages and other negative impacts on organizations.
- To prevent falling victim to phishing scams, it is important to never provide personal information, contact legitimate organizations, and report phishing emails and messages.
- Staying vigilant and taking proactive steps to protect yourself and your organization from these attacks is crucial.
- Phishing attacks can be mitigated by following best practices, such as verifying the legitimacy of requests, contacting legitimate organizations, and reporting phishing emails and messages.
- By staying informed and taking the necessary precautions, we can all help to mitigate the risk of falling victim to these scams.
Why Be Proactive and Vigilant ?
Phishing scams are getting more frequent and complex. It’s high time people must be aware of the types of phishing attempts. Understanding these tactics can help you better prepare yourself to stay online secure and keep your confidential information safe.
The following points will highlight the significance of being proactive and vigilant:
Recognizing Red Flags: Understanding the different types of phishing attacks allows you to identify warning signs. Knowing what to look for in a deceptive email, a malicious website, or a fraudulent phone call can help you avoid falling victim to scams.
Enhancing Security Awareness: Being aware of common phishing techniques raises your overall security consciousness. It encourages you to adopt proactive measures and stay vigilant while interacting with emails, websites, and online platforms.
Protecting Personal Information: Phishing attacks frequently attempt to steal sensitive information such as passwords, credit card information, or social security numbers. Knowing the different types of attacks allows you to anticipate situations in which you may be asked to disclose such confidential information.
Safeguarding Financial Assets: Phishing attacks targeting online banking and financial transactions can lead to significant monetary losses. By understanding these attacks, you can actively implement security measures to protect your financial assets and prevent unauthorized access.
Preserving Digital Identity: Phishing attempts can compromise your online identity, resulting in illegal account access, identity theft, or reputational damage. You can protect your digital identity and online privacy by being updated on typical attack vectors.
Reporting and Taking Action: Understanding different phishing strategies enables you to appropriately report events. By promptly reporting phishing assaults, you can help take down bogus websites, raise awareness, and potentially prevent future attacks.
Remember to stay up to date on the newest trends and emerging phishing strategies, as fraudsters are always adapting their methods. All of us can contribute to making the internet a safer place by educating ourselves and others about common phishing attack types. Stay alert and protect yourself from the constant threat of phishing attempts.
In this post, we will discuss the most frequent types of phishing attempts, including time-tested methods and social engineering techniques used by attackers. Those who understand these techniques can better protect themselves from becoming victims of phishing schemes.
Strategies Used in Phishing Attacks
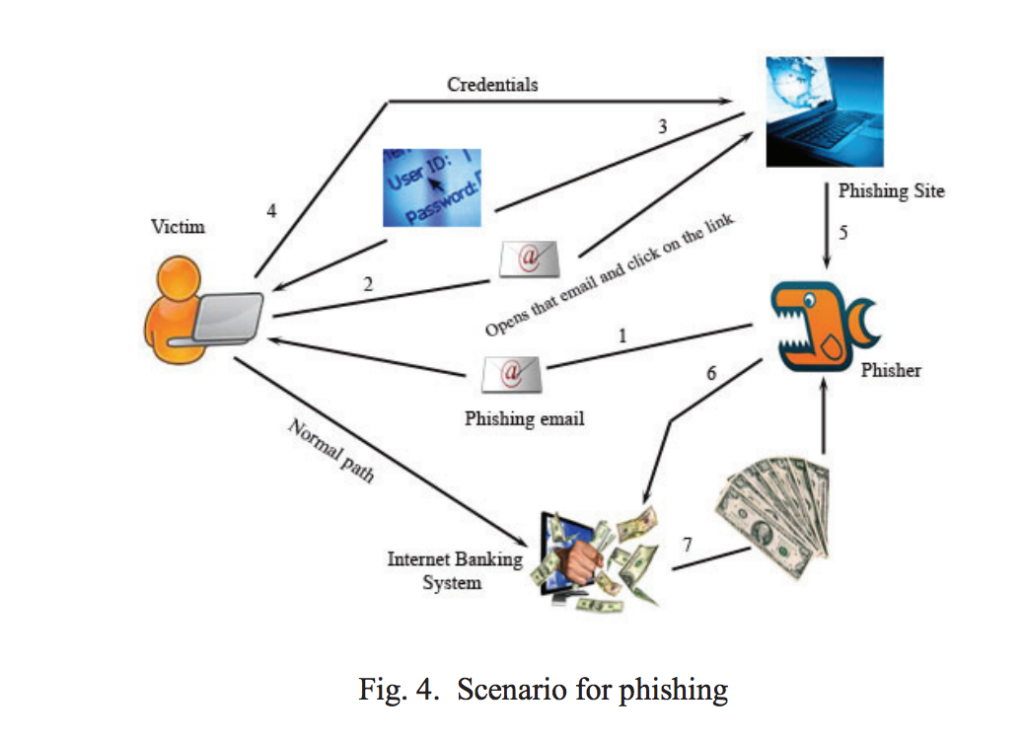
Phishing attacks are becoming increasingly sophisticated, and attackers are using a variety of tactics to trick individuals into divulging sensitive information. Here are some examples of phishing emails and text messages that attackers commonly use:
A. Email Phishing
Phishing emails are a prevalent sort of cyberattack that uses false emails to fool a victim into divulging personal information or performing unapproved acts.
Attackers frequently establish a false sense of legitimacy and compel the victim to act right away by using phishing URLs, fake emails, and an urgency that can’t be ignored.
Email phishing attempts can take many different forms, such as spoofing emails from reliable sources, phishing links that lead to fraudulent websites intended to steal information, and urgent calls to action such as saying the recipient’s account has been hijacked.
B. Spear Phishing
Spear phishing is a type of phishing that targets specific individuals or groups inside an organization, leveraging tailored information to boost the likelihood of a successful attack.
Attackers use social engineering techniques to construct tailored and convincing messages that frequently include the target’s name and rank within the firm, creating a false impression of legitimacy.
Spear phishing attacks comprise emails including precise information about the target, such as their name and function within the organization, as well as statements intended to fool the receiver into doing unauthorized activities or disclosing sensitive information.
C. Smishing and Vishing
Smishing and vishing are types of phishing that use text messages (smishing) and voice calls (vishing) to trick people into disclosing sensitive information or performing unwarrented acts.
Attackers frequently employ a sense of urgency and faked numbers to create a false sense of legitimacy and compel the recipient to act immediately.
Smishing and vishing assaults involve urgent calls to action, such as stating the recipient’s account has been compromised, as well as communications that attempt to deceive the recipient into disclosing sensitive information or conducting unlawful acts.
Individuals can better protect themselves against phishing scams by becoming aware of these prevalent strategies. When receiving unwanted emails or text messages, always exercise caution and never submit sensitive information without authenticating the request.
Impact of Phishing Attacks
Phishing assaults can have serious repercussions, including money losses, psychological suffering, and decreased productivity. Falling prey to phishing scams can lead to identity theft, bringing serious harm to people. Financial data, such as banking logins, PINs, account numbers, and credit card information, are frequently targeted by phishers, posing a substantial threat to the financial industry.
Ransomware is a peculiar example of malware and phishing which has emerged as a major threat. All organizations must mitigate risk due to the method by which ransomware and other viruses are delivered. These attacks can result in direct cash losses, regulatory fines, and long-term reputational damage.
Phishing assaults can interrupt a company’s operations, install malware or ransomware, and harm its reputation. Criminals are becoming increasingly skilled and creative, making it tough to detect and thwart phishing attempts. Once an attacker has gained access to a network, they can install malware or ransomware, resulting in system outages and other undesirable disturbances. Phishing assaults can also cause decreased productivity, absenteeism, and other negative effects on a person’s employment. Organizations must comply with regulations, data protection, and privacy policies, as well as cybersecurity standards to keep consumer data secure.
Individuals must exercise caution when receiving unsolicited emails or text messages, and they should never submit sensitive information without first checking the veracity of the request. Individuals and organizations can protect themselves from phishing attempts by understanding the impact they have.
Prevention and Mitigation of Phishing Attacks
Phishing attacks can be avoided and alleviated by adopting proactive steps. Here are a few excellent practices to follow:
Preventive Measures
Never provide personal information to unknown sources or unsolicited requests. Phishers frequently utilize social engineering strategies to deceive people into disclosing sensitive information, which can result in identity theft and financial damages.
Personal information should not be shared in job applications, unwanted phone calls or emails, online surveys, or social media quizzes. Before submitting any personal information, make sure the request and the organization are legitimate.
Reporting of Suspicious Phishing Activities
Legitimate institutions should be contacted in circumstances such as suspicious emails claiming to be from a bank or financial institution, requests for personal information from unknown sources, and unwanted emails or messages seeking immediate action.
Any suspicious phishing emails or messages should be reported to the legitimate organization’s security staff, the Anti-Phishing Working Group, or the Federal Trade Commission. It is critical to avoid clicking on links or downloading attachments from dubious emails or messages.
Reporting phishing emails and messages can help others from falling victim to the same assault. It can also help organizations and law enforcement agencies detect and analyze phishing attempts.
Individuals and organizations can avoid falling victim to phishing attacks by implementing these preventative and mitigation methods. It is critical to remain watchful and careful when receiving unsolicited emails or texts, as well as to confirm the authenticity of any requests for personal information.
Frequently Asked Questions (FAQ)
- Q1: What is phishing?
- A1: Phishing is a type of cyber attack that uses deceptive emails, text messages, or phone calls to trick individuals into revealing sensitive information or taking unauthorized actions.
- Q2: What are the most common types of phishing attacks?
- A2: The most common types of phishing attacks include email phishing, spear phishing, smishing, and vishing.
- Q3: What are the common tactics used in phishing attacks?
- A3: Common tactics used in phishing attacks include creating a sense of urgency, using character substitution in domain names, and spoofing legitimate sources.
- Q4: What are the consequences of falling victim to phishing scams?
- A4: Falling victim to phishing scams can lead to financial losses, mental distress, and productivity decline. Financial data, such as banking logins, PINs, account numbers, and credit card details, are often targeted by phishers.
- Q5: What is ransomware, and how does it relate to phishing attacks?
- A5: Ransomware is a type of malware that encrypts a victim’s files and demands payment in exchange for the decryption key. Ransomware is often distributed through phishing attacks.
- Q6: Why should personal information never be provided?
- A6: Personal information should never be provided to unknown sources or unsolicited requests. Phishers often use social engineering tactics to trick individuals into revealing sensitive information, which can lead to identity theft and financial losses.
- Q7: Why should legitimate organizations be contacted?
- A7: If an individual receives a suspicious email or message, they should contact the legitimate organization directly to verify the authenticity of the request. This can help prevent falling victim to a phishing attack.
- Q8: Why should phishing emails and messages be reported?
- A8: Reporting phishing emails and messages can help prevent others from falling victim to the same attack. It can also help organizations and law enforcement agencies track and investigate phishing attacks.
- Q9: What is the importance of staying vigilant and taking proactive steps to prevent falling victim to phishing scams?
- A9: By staying vigilant and taking proactive steps to protect yourself and your organization from these attacks, we can all help to mitigate the risk of falling victim to these scams.
Conclusion
Phishing attacks are a prevalent and ongoing threat to individuals and businesses alike. In this article, we looked at the most prevalent forms of phishing attacks and strategies, such as email phishing, spear phishing, smishing, and vishing. We also covered the consequences of falling prey to phishing scams, such as financial data theft and the spread of ransomware and other viruses.
To avoid falling prey to phishing attacks, never submit personal information, only contact legitimate businesses, and report phishing emails and messages. It is also critical to remain attentive and take proactive measures to defend yourself and your company from these threats.
To summarize, phishing assaults are a severe risk that requires ongoing attention and awareness. By remaining enlightened and taking the required precautions, we can all help to alliviate our chances of falling victim to these frauds.
Phishing Quiz
- Which of the following is a common tactic used in email phishing attacks?
- a. Sending emails with generic subject lines and content to a wide audience
- b. Registering fake domains that mimic legitimate organizations
- c. Using character substitution in domain names to deceive recipients
- d. Creating a sense of urgency to prompt immediate action
- Spear phishing is a type of phishing attack that:
- a. Targets a specific individual or organization
- b. Uses generic emails with no personalized information
- c. Is less sophisticated than email phishing
- d. Is not a common form of phishing attack
- Smishing is a type of phishing attack that:
- a. Uses emails to deceive recipients
- b. Uses text messages to deceive recipients
- c. Is not a common form of phishing attack
- d. Is less sophisticated than email phishing
- Vishing is a type of phishing attack that:
- a. Uses emails to deceive recipients
- b. Uses text messages to deceive recipients
- b. Uses voice calls to deceive recipients
- d. Is not a common form of phishing attack
- Angler phishing is a type of phishing attack that:
- a. Uses emails to deceive recipients
- b. Uses text messages to deceive recipients
- c. Uses voice calls to deceive recipients
- d. Uses social media to deceive recipients
- Which of the following is a common tactic used in spear phishing attacks?
- a. Sending emails with generic subject lines and content to a wide audience
- b. Registering fake domains that mimic legitimate organizations
- c. Using character substitution in domain names to deceive recipients
- d. Sending emails with generic subject lines and content to a wide audience
- Which of the following is a common tactic used in smishing attacks?
- a. Sending emails with generic subject lines and content to a wide audience
- b. Registering fake domains that mimic legitimate organizations
- c. Using character substitution in domain names to deceive recipients
- d. Using text messages with generic content to a wide audience
- Which of the following is a common tactic used in vishing attacks?
- a. Sending emails with generic subject lines and content to a wide audience
- b. Registering fake domains that mimic legitimate organizations
- c. Using character substitution in domain names to deceive recipients
- d. Using voice calls with generic content to a wide audience
- Which of the following is a common tactic used in angler phishing attacks?
- a. Sending emails with generic subject lines and content to a wide audience
- b. Registering fake domains that mimic legitimate organizations
- c. Using character substitution in domain names to deceive recipients
- d. Using social media with generic content to a wide audience
- Which of the following is a common tactic used in phishing attacks to create a sense of urgency?
- a. Sending emails with generic subject lines and content to a wide audience
- b. Creating a sense of urgency to prompt immediate action
ANSWERS
- a
- a
- b
- b
- b
- b
- b
- b
- b
- b
